Mac
Macintosh Hacking
Macintosh SE Video interface
 |
 |
Rather than let an old Mac SE with dead drives go to waste, I built a video card interface to the BeagleBone Black to drive the 512x342x1 display using the PRU. Read on for more info...
ADB to USB adapter
 Older Macintosh computers used the Apple Desktop Bus protocol to communicate with keyboards and mice. It is a one-wire, bidirectional multi-drop protocol. More information on my adapter design
Older Macintosh computers used the Apple Desktop Bus protocol to communicate with keyboards and mice. It is a one-wire, bidirectional multi-drop protocol. More information on my adapter design
Mac SE Easter Egg
 |
 |
Using my PROMdate generic EPROM reader, I extracted the Mac SE boot ROMs from a machine I found on the side of the road. We then reverse engineered the easter egg photographs of the development team hidden in the extra space. Read on for more details...
Mac EFI firmware
 Thunderstrike is the name for a class of Apple EFI firmware security vulnerabilities that allow malicious software or Thunderbolt devices to flash untrusted code to the boot ROM and propagate via shared devices. It was presented at 31C3. Read on for more info on Thunderstrike or Thunderstrike 2, a software-only extension.
Thunderstrike is the name for a class of Apple EFI firmware security vulnerabilities that allow malicious software or Thunderbolt devices to flash untrusted code to the boot ROM and propagate via shared devices. It was presented at 31C3. Read on for more info on Thunderstrike or Thunderstrike 2, a software-only extension.
 Thunderstrike 2 was presented at DefCon 23 / BlackHat 2015 and the annotated presentation is available with significantly more details, as well as a demo video of the proof-of-concept in action. Thunderstrike 2 is a continuation of my security research on Thunderstrike, in collaboration with Xeno Kovah and Corey Kallenberg of LegbaCore. I've also collected Thunderstrike 2 news coverage.
Thunderstrike 2 was presented at DefCon 23 / BlackHat 2015 and the annotated presentation is available with significantly more details, as well as a demo video of the proof-of-concept in action. Thunderstrike 2 is a continuation of my security research on Thunderstrike, in collaboration with Xeno Kovah and Corey Kallenberg of LegbaCore. I've also collected Thunderstrike 2 news coverage.
Vulnerability status
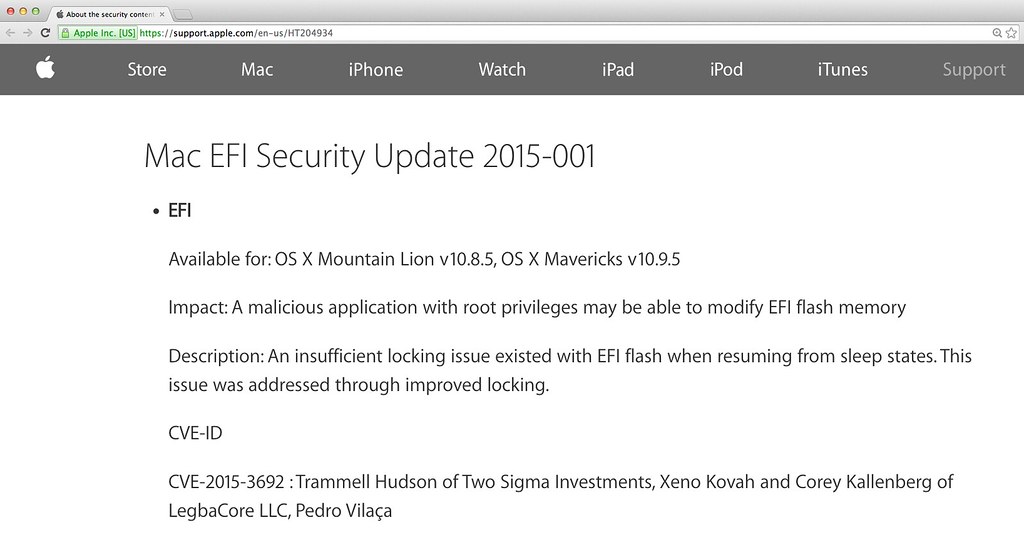 Thunderstrike 2 was partialy fixed as part of Mac EFI Security Update 2015-001 in June 2015 (VU#577140, CVE-2015-3692). Systems running OS X 10.10.4 and higher are no longer trivially vulnerable. "Partially patched" means that the Protected Range Registers (PRR) are locked before the S3 script is run, which prevents a Darth Venamis "Dark Jedi" attack on the boot flash, but it does not fix several other issues. We have disclosed the following remaining problems to Apple's product firmware security team:
Thunderstrike 2 was partialy fixed as part of Mac EFI Security Update 2015-001 in June 2015 (VU#577140, CVE-2015-3692). Systems running OS X 10.10.4 and higher are no longer trivially vulnerable. "Partially patched" means that the Protected Range Registers (PRR) are locked before the S3 script is run, which prevents a Darth Venamis "Dark Jedi" attack on the boot flash, but it does not fix several other issues. We have disclosed the following remaining problems to Apple's product firmware security team:
- Option ROMs are still loaded during normal boots. Snare's 2012 Option ROM attack still works and could be extended to other Option ROMs built into the system's WiFi or video card.
- The S3 resume bootscript is still unprotected and executes code from RAM, allowing code injection into PEI from either a software attack or an Option ROM attack.
BIOS_CNTL.BLEandBIOS_CNTL.SMM_SWPare not locked, allowing the NVRAM to be corrupted (and leaving open possible attacks on the PRR).TSEGMBis left unlocked, allowing DMA into SMRAM and code injection into SMM.- And there some other issues that we haven't fully tested.
Even with the patch applied, it is still possible for Thunderstrike 2 to write to Option ROMs and continue to spread to new machines, to persist in the S3 resume script until the next full reboot, to hide in System Management mode and evade detection from software scanning, and to "irrevocably" brick systems by corrupting NVRAM.
2015 Security Reverse engineering