BH2019
2019 Security Conferences These are some talks that I found interesting at BlackHat 2019.
Breaking Samsung's ARM TrustZone
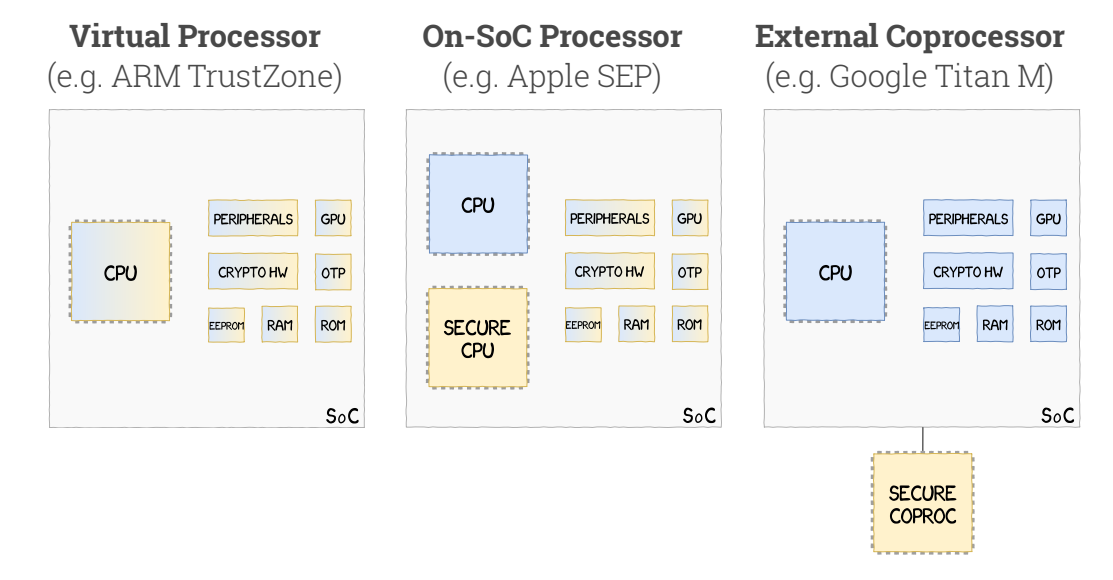
Quarkslab (Peterlin, Adamski & Guilbon) Slides, with xkcd-style diagrams.
They built a ghidra parser for the "Kinibi" trusted OS and were able to use AFL + Manticore to locate vulnerabilities (memcpy()!) that gave them execution all the way into the secure monitor.
Behind the scenes of Intel's ME
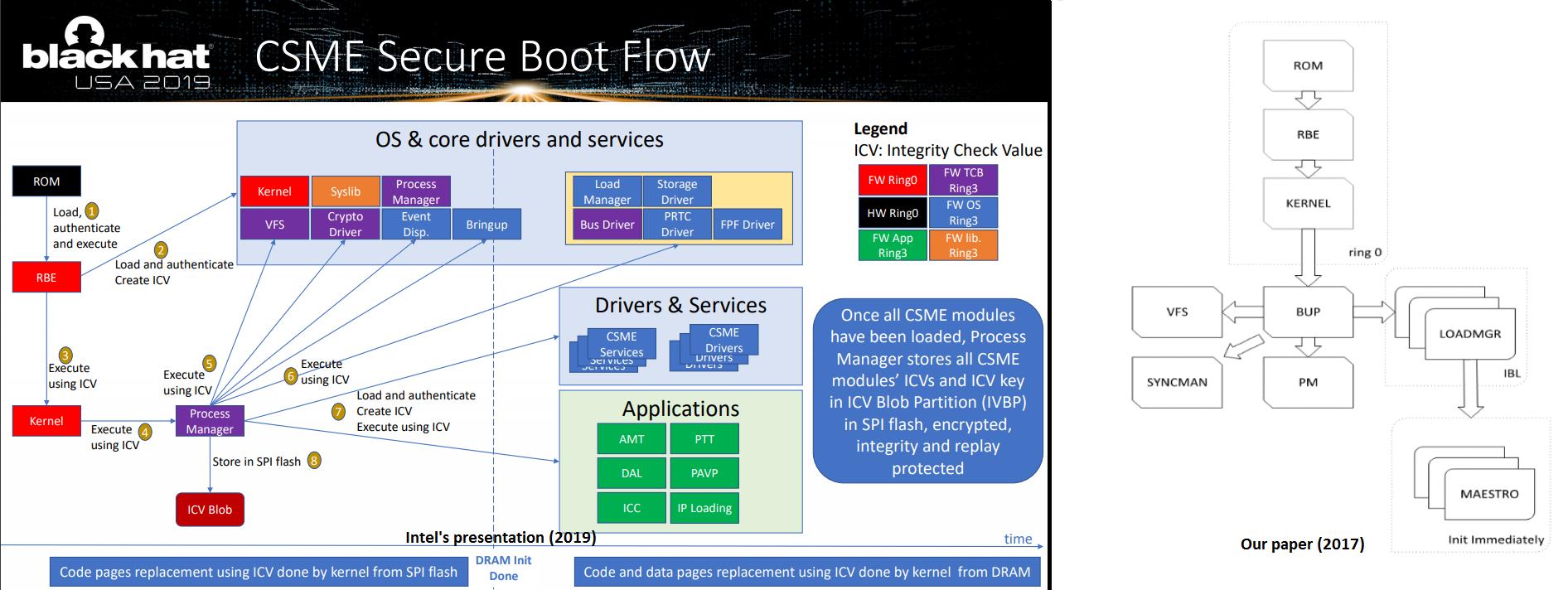
Intel (Hasarfaty & Moyal) Slides. Lots of very interesting details, including boot flow diagrams and confirmation of the Minix rumors. Still many questions, but worth reading.
Maxim Goryachy asks some of those questions, such as why isn't HAP documented, why the IDLM debug module has access to the chipset key, and if they plan to add ASLR.
I'm curious about the interactions with SGX (implemented via DAL), the CPU uCode and FIT interactions during bootup, and things like the Widevine (PVP/DRM) interactions with the rest of the system.
Inside the Apple T2
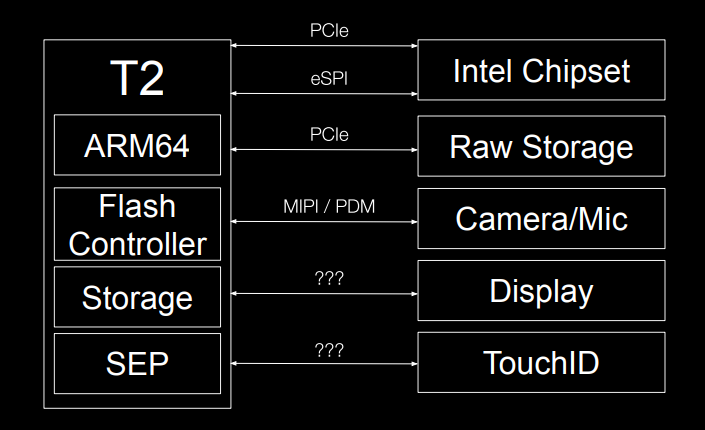
Duo Labs (Davidov & Erikson) Slides. Deep dive into the T2's eSPI secure boot on the Macbooks and the communication between the kernel and the T2 coprocessor. Reuses one of my photos of the older SPI flash chips. Clearly we need to update spispy to work with eSPI so that we can log it / MITM / TOCTOU the boot process.
The Enemy Within: Modern Supply Chain Attacks
Microsoft Security (Doerr) Slides The Supply Chain is not just manufacturing - it is people, software, services, and hardware. Interestingly, MS did find an IoT attack on their networks.
Breaking Through Another Side
Matrosov & Gazet Slides. They examined the hardware security of the numerous CPUs in a modern laptop and point out that most of those chips are "Not under direct control from laptop vendors Involved in security features implementation, Connected to UEFI firmware (BIOS), Considered to generate trusted I/O, Mostly out of the supervision scope of the main CPU". This is not fine. They cite works like TPMGenie and my TOCTOU as examples of where the security boundaries are not well defined. In the case of the Embedded Controller (EC), they found really bad things like shared secrets stored in the BIOS.

The team also examined Intel BIOS Guard ACM and found that it was encrypted, which is unexpected. The Intel security technologies seems to be the only public discussion of BIOS Guard and how it interacts with the EC. This also might remove the need for SMM BIOS write control bits since the SPI flash can only be written from the BIOS Guard ACM. It also mentions that the ACM provisions a shared secret to the EC for authenticating future flash accesses; perhaps that is the need for encrypting the ACM if the secret is fixed.
Firmware Cartography
Atredis Partners (Keltner & Blazakis) (No slides yet)
The modern server is the Matryoshka doll of computers, computers inside computers, a giant, undocumented mess. Undocumented devices have made homes at undocumented addresses, on buses, and in protocols most server owners don't know exist. With few exceptions, however, they and their secrets can't really stay hidden -- you just have to know how to look.
Defeating Cisco Trust Anchor
Red Balloon Security (No slides yet). Cisco is using an FPGA to validate their system's firmware, but the bitstream is writable from the host, so if an attacker can get code execution on the main CPU or are physically proximate, they can disable the Trust Anchor by writing an FPGA bitstream that doesn't check signatures, etc. Wow.